I’ve been experiencing, for months and months, quite violent OSX crashes, attributed to the GPU.
My awesome friend Dennis suggested me to try disabling Integrated <> Discrete GPU switching. And guess what? i’ve been crash free for almost two weeks.
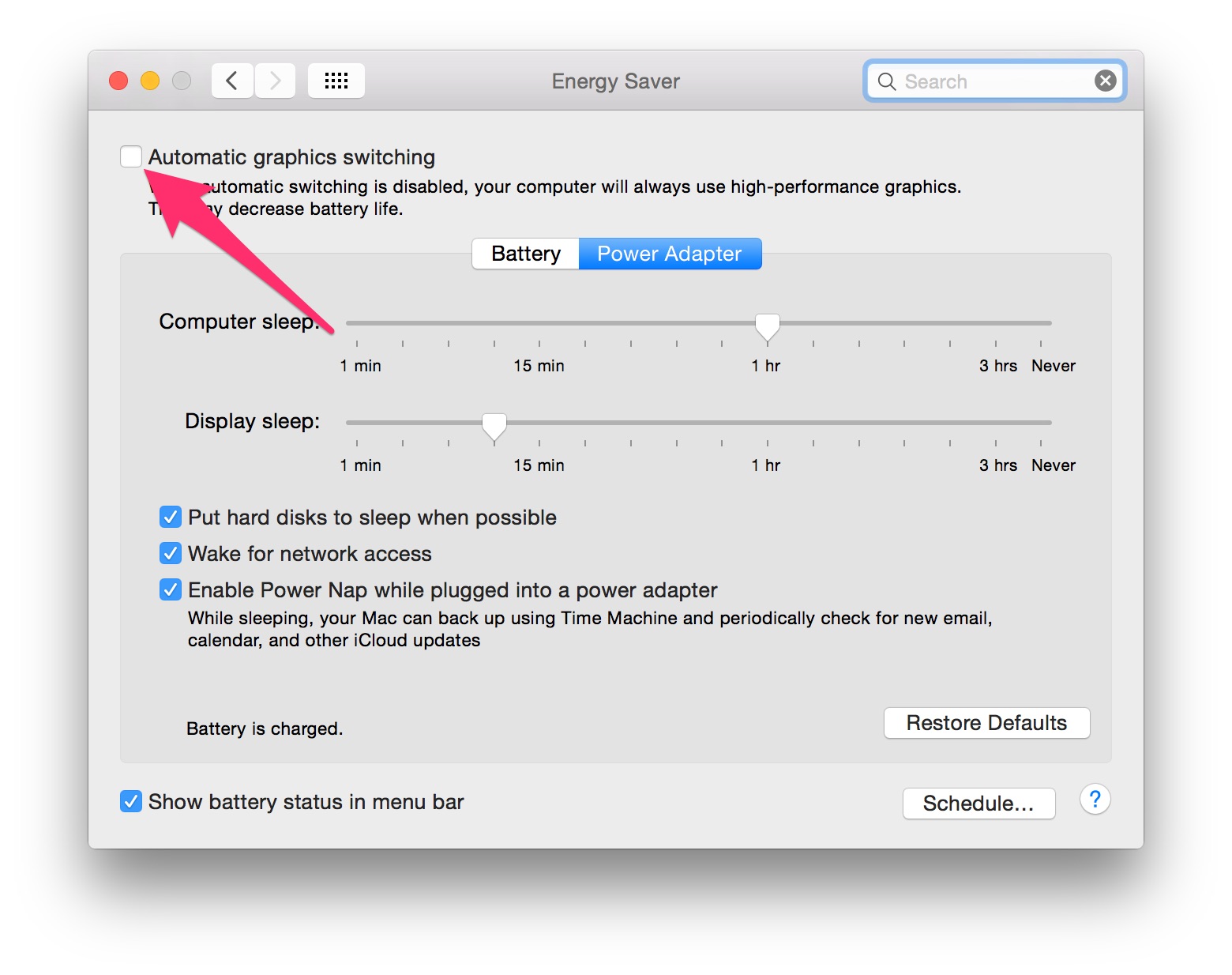
I’m just documenting right here what has to be done, for future reference. Just uncheck this Energy Preference.
I’ve been told that the exact string for the checkmark might look different across the latest Yosemite releases, but the setting should still be lurking there:
P.s.: Again, thank you Dennis!!