If you’re reading this post, you’re probably aware of the dangers of Flash Player. And you’ve read, most probably, about the last couple of viruses / penetrations to Facebook and Google.
Steve Jobs hated Adobe Flash… personally, i say he had a very good reason. If wasn’t, probably, just because Adobe refused (at first) to publish its suite for Mac. He knew that it was troublesome… so… let’s proceed removing that junk from our system!.
First: Download the Uninstaller
If you’re running Snow Leopard (or newer), you’re gonna need to download the Flash Player Uninstaller. However, if you’re running an older version (Leopard and Tiger), please, download this uninstaller.
You’re gonna need to double click on the DMG file, and click on the “Adobe Flash Player Uninstaller” application. You should get the following window onscreen:
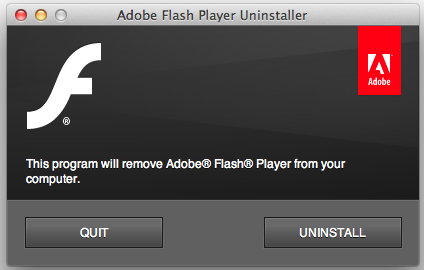
Second: Proceed uninstalling
This is pretty straightforward. Simply hit the ‘Uninstall’ button, and it will all be over, soon enough. You will be required to close all of your browsers first. Once it’s all over, you should see the following screen:

Congratulations! welcome to the future!. HTML 5 is becoming the web standard… and we certainly don’t need Adobe to run anything on a browser.
Like this:
Like Loading...